Table of Contents
Tools for IPV6
Linux
ping6 -i eth0 ff02::1 ping6 -B -I eth0 -I [global IPv6 address attached to eth0] ff02::1 ip -o -f inet6 addr ip -f inet6 neighbor ip -6 neighbor show
Mac
iMac:~ andrew$ ndp -a
Windows
ping -S [global IPv6 address] -6 ff02::2 netsh interface ipv6 show neighbors netsh interface ipv6 show interface "Local Area Connection* 1" netsh interface ipv6 show interface netsh interface ipv6 delete neighbors
From: http://billspeers.com/?q=node/259
nmap -6 --script=broadcast-dhcp6-discover netsh int ipv6 show prefixpolicies netsh interface ipv6 show address netsh interface ipv6 show interface netsh interface ipv6 show neighbors netsh interface ipv6 delete neighbors netsh interface ipv6 show destinationcache netsh interface ipv6 delete destinationcache netsh interface ipv6 show route netsh interface ipv6 show joins netsh interface ipv6 show ipstats netsh interface ipv6 show global Netsh dns show state route print tracert Pathping ping ipconfig /displaydns
Powershell
Get-Netneighbor -InterfaceIndex 4 -AddressFamily IPv6
nmap
nmap -PN -sT 2001:1::2/64 -p 3389 nmap -6 --script=targets-ipv6-multicast-echo.nse --script-args 'newtargets' -sL -d1 -oA c:\temp\nmap.txt nmap -6 --script=targets-ipv6-multicast-echo.nse --script-args 'newtargets,interface=eth2' -sL nmap -sU -p 10001 --script=ubiquiti-discovery.nse 10.2.2.0/24
2020-12-08 File targets-ipv6-multicast-invalid-dst Script types: prerule Categories: discovery, broadcast Download: https://svn.nmap.org/nmap/scripts/targets-ipv6-multicast-invalid-dst.nse User Summary Sends an ICMPv6 packet with an invalid extension header to the all-nodes link-local multicast address (ff02::1) to discover (some) available hosts on the LAN. This works because some hosts will respond to this probe with an ICMPv6 Parameter Problem packet.
From <https://nmap.org/nsedoc/scripts/targets-ipv6-multicast-invalid-dst.html>
File targets-ipv6-multicast-echo Script types: prerule Categories: discovery, broadcast Download: https://svn.nmap.org/nmap/scripts/targets-ipv6-multicast-echo.nse User Summary Sends an ICMPv6 echo request packet to the all-nodes link-local multicast address (ff02::1) to discover responsive hosts on a LAN without needing to individually ping each IPv6 address.
From <https://nmap.org/nsedoc/scripts/targets-ipv6-multicast-echo.html>
/dSploit/jni/nmap/scripts/targets-ipv6-multicast-echo.nse
https://github.com/simpleverso/dsploit
From <http://138.201.16.208/file/86135700/>
• nmap • scripts • targets-ipv6-multicast-echo.nse Find fileBlameHistoryPermalink Imported Upstream version 7.00
Linux Simply use the native ping and ip commands. ping -6 -I <INTERFACE> ff02::1 ping -6 -I <INTERFACE> ff02::2 ip neigh
From <https://pwn.no0.be/recon/network/neighbor_discovery/>
Linux and Mac
v6disc.sh
2020-08-01
Synopsis
A shell script to quickly & automatically discover IPv6 hosts, with the option to ping or run nmap against discovered hosts.
Motivation
There are three reasons to use v6disc.sh
1. Scan an IPv6 network 700,000 times faster than nmap 2. Auto Discovery of IPv6 hosts on the network (e.g. for IPAM) 3. Quickly figure out what IPv6 is already on your network.
With 18,446,744,073,709,551,616 (2^64) potential addresses on a LAN segment, the old brute force method of scanning every address (e.g. with nnap) quickly becomes impractical. Even with version 7 of nmap, scanning a /64 still takes a week! v6disc.sh scans a /64 less than 5 seconds.
From <https://github.com/cvmiller/v6disc>
./v6disc.sh -h
./v6disc.sh - auto discover IPv6 hosts
e.g. ./v6disc.sh -D -p
-p Ping discovered hosts
-i use this interface
-L show link-local only
-D Dual Stack, show IPv4 addresses
-N Scan with nmap -6 -sT
-q quiet, just print discovered hosts
Scamper measurement of connection information
From: http://www.caida.org/tools/measurement/scamper/
IPv6 and IPv4 active traceroute probing and ping
Scamper is designed to actively probe destinations in the Internet in parallel (at a specified packets-per-second rate) so that bulk data can be collected in a timely fashion. Scamper's native output file format is called warts: a warts file contains substantial meta data surrounding each individual measurement conducted, as well as substantial detail of responses received. The measurements conducted can range from simple to complex. An example of a simple measurement is where a single measurement method (e.g. traceroute) is used on a list of IP addresses to conduct a bulk measurement. A more complex measurement might be where the outcome of a previous test influences what happens next: for example, for each hop in a traceroute path, infer the address of the outgoing interface for the previous hop. Complex measurements are conducted by connecting to a running scamper process with a driver program which contains the logic.
Network Troubleshooting Tools, IPv4 and IPv6
Windows: Vista, 7, Server 2008 and higher
Ping for IPv4 ping -4 Ping for IPv6 ping -6 Traceroute for IPv4 tracert -4 Traceroute for IPv6 tracert -6 Interface Info ipconfig /all IPv4 Route table netsh interface ipv4 show route IPv6 Route table netsh interface ipv6 show route IPv4 arp table arp -a IPv6 ndp table netsh interface ipv6 show neighbors
IPv6 Neighbor Discovery Mechanisms
There are nine Neighbor Discovery mechanisms that are implemented using the various Neighbor Discovery messages. These mechanisms are at the heart of IPv6. The Neighbor Discovery mechanisms are: Router Discovery Prefix Discovery Parameter Discovery Stateless Address Autoconfiguration (SLAAC) Address Resolution (mapping IPv6 addresses to Link Layer addresses) Next Hop Determination Neighbor Unreachability Detection (NUD) Duplicate Address Detection (DAD) Redirect
Well-known IPv6 multicast addresses
From: http://en.wikipedia.org/wiki/Multicast_address
Address Description
ff02::1 All nodes on the local network segment
ff02::2 All routers on the local network segment
ff02::5 OSPFv3 All SPF routers
ff02::6 OSPFv3 All DR routers
ff02::8 IS-IS for IPv6 routers
ff02::9 RIP routers
ff02::a EIGRP routers
ff02::d PIM routers
ff02::16 MLDv2 reports (defined in RFC 3810)
ff02::1:2 All DHCP servers and relay agents on the local network segment (defined in RFC 3315)
ff02::1:3 All LLMNR hosts on the local network segment (defined in RFC 4795)
ff05::1:3 All DHCP servers on the local network site (defined in RFC 3315)
ff0x::c Simple Service Discovery Protocol
ff0x::fb Multicast DNS
ff0x::101 Network Time Protocol
ff0x::108 Network Information Service
ff0x::181 Precision Time Protocol (PTP) version 2 messages (Sync, Announce, etc.) except peer delay measurement
ff02::6b Precision Time Protocol (PTP) version 2 peer delay measurement messages
ff0x::114 Used for experiments
Address Description
ff02:0000:0000:0000:0000:0000:0000:0001 All nodes on the local network segment
ff02:0000:0000:0000:0000:0000:0000:0002 All routers on the local network segment
ff02::5 OSPFv3 All SPF routers
ff02::6 OSPFv3 All DR routers
ff02::8 IS-IS for IPv6 routers
ff02::9 RIP routers
ff02::a EIGRP routers
ff02::d PIM routers
ff02::16 MLDv2 reports (defined in RFC 3810)
ff02:0000:0000:0000:0000:0000:0001:0002 All DHCP servers and relay agents on the local network segment
(defined in RFC 3315)
ff02:0000:0000:0000:0000:0000:0001:0003 All LLMNR hosts on the local network segment (defined in RFC 4795)
ff05:0000:0000:0000:0000:0000:0001:0003 All DHCP servers on the local network site (defined in RFC 3315)
ff0x::c Simple Service Discovery Protocol
ff0x::fb Multicast DNS
ff0x::101 Network Time Protocol
ff0x::108 Network Information Service
ff0x::181 Precision Time Protocol (PTP) version 2 messages (Sync, Announce, etc.) except peer delay measurement
ff02::6b Precision Time Protocol (PTP) version 2 peer delay measurement messages
ff0x::114 Used for experiments
ipv6 testing windows command line
From: http://billspeers.com/?q=node/259
nmap -6 --script=broadcast-dhcp6-discover
netsh int ipv6 show prefixpolicies
netsh interface ipv6 show address
netsh interface ipv6 show interface
netsh interface ipv6 show neighbors
netsh interface ipv6 delete neighbors
netsh interface ipv6 show destinationcache
netsh interface ipv6 delete destinationcache
netsh interface ipv6 show route
netsh interface ipv6 show joins
route print
tracert
Pathping
Ping
ipconfig /displaydns
netsh interface ipv6 show ipstats
netsh interface ipv6 show global
Netsh dns show state
Name Resolution Policy Table Options
Query Failure Behavior : Always fall back to LLMNR and NetBIOS if the name does not exist in DNS
or if the DNS servers are unreachable when on a private network
Query Resolution Behavior : Resolve only IPv6 addresses for names
Network Location Behavior : Never use Direct Access settings
Machine Location : Outside corporate network
Direct Access Settings : Configured and
From: https://technet.microsoft.com/en-us/library/ee624049(v=ws.10).aspx
nslookup for ipv6 use the –q=aaaa command-line parameter to request only IPv6 addresses in the response. The syntax is nslookup –q=aaaa IntranetFQDN IntranetDNSServerIPv6Address (example: nslookup –q=aaaa dc1.corp.contoso.com 2002:836b:2:1::5efe:10.0.0.1). nslookup isp.test-ipv6.com nslookup Domain.com 2001:4860:4860::8888 nslookup -q=aaaa Domain.com 2001:4860:4860::8888 nmap -6 --script=targets-ipv6-multicast-echo.nse --script-args 'newtargets' -sL -d1 -oA c:\\temp\\nmap.txt
pfsense ipv6 with comcast
From: http://undergroundmod.com/2016/08/25/pfsense-ipv6-with-comcast/
From: https://r.wundrd.net/article/pfsense-ipv6-comcast/
go to Status: Interfaces page. Under your WAN interface section, you should see an IPv6 address (in addition to link local), a subnet mask ipv6 of 64, and a gateway ipv6. Note the ISP DNS Servers section should contain ipv6 addresses. Record one of those for later testing. Under the LAN interface section, you should see an IPv6 address (in addition to link local), and a subnet mask ipv6 of 64
netconf
From: http://www.v6edu.com/index.php/products/99-netconf
Also: http://www.v6edu.com/images/apps/NetConf32.msi
NetConf is a native (non-Web) application for Windows Vista and Windows Server 2008 or later that provides a GUI alternative to the netsh command line interface. It provide much more control and information than the Microsoft supplied GUI network management tools, especially for IPv6. NetConf will run and install on Windows XP and Windows Server 2003 but some of the advanced functions will not work due to missing IPv6 functionality on those platforms. For example, on those platforms you cannot disable Router Discovery, so SLAAC will always happen. You can disable Prefix Information being sent in Router Advertisements on some IPv6 routers or firewalls to stop SLAAC from happening, but that will affect all nodes in the subnet.
NetConf Dual Stack Network Configuration
From: http://www.sixscape.com/joomla/sixscape/index.php/products
NetConf is a native (non-Web) application for Windows Vista and Windows Server 2008 or later that provides a GUI alternative to the netsh command line interface. It provide much more control and information than the Microsoft supplied GUI network management tools, especially for IPv6. NetConf will run and install on Windows XP and Windows Server 2003 but some of the advanced functions will not work due to missing IPv6 functionality on those platforms. For example, on those platforms you cannot disable Router Discovery, so SLAAC will always happen. You can disable Prefix Information being sent in Router Advertisements on some IPv6 routers or firewalls to stop SLAAC from happening, but that will affect all nodes in the subnet.
Link Local Multicast Name Resolution
Now that DNS name resolution has failed, the computer will send a multicast name query out using the UDP protocol. All of the other devices on the network will receive the query. Assuming that these computers are running Windows Vista or Longhorn Server (meaning that they are link local multicast name resolution enabled), they will compare the query to their own host name. Assuming that the requested host is not prohibited from responding to link local multicast name resolution queries, the computer will send a unicast message to the computer that sent the query. This message will contain the host’s IP address.
IPv6 Stateless Address Autoconfiguration (SLAAC)
From: https://www.youtube.com/watch?v=zbkBa8Zl568
From: https://tools.ietf.org/html/rfc4862 Good info
Addresses are generated by Host
The stateless mechanism allows a host to generate its own addresses using a combination of locally available information and information advertised by routers. Routers advertise prefixes that identify the subnet(s) associated with a link, while hosts generate an "interface identifier" that uniquely identifies an interface on a subnet. An address is formed by combining the two. In the absence of routers, a host can only generate link-local addresses. However, link-local addresses are sufficient for allowing communication among nodes attached to the same link.
DAD Duplicate Address Discovery
From: https://www.youtube.com/watch?v=O1JMdjnn0ao
notice to exclude solicited Node Multicast address FF02::1:FFxx:xxxx from filter sent to
ff02::16 MLDv2 reports
multicast IPv6 match last 32 bits of layer 2 address 33:33:00:00:00:16
IPv6 Addressing (TechRef)
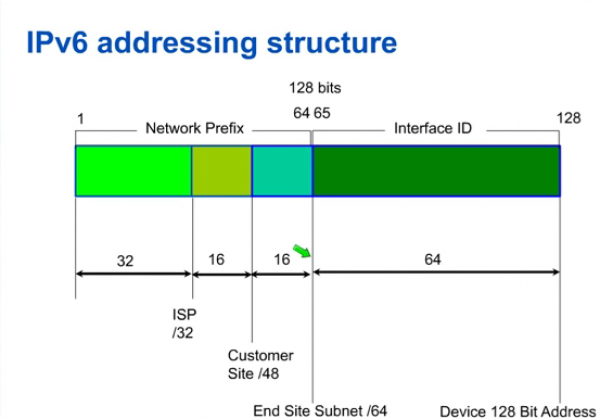
IPv6 Addressing Structure
Link-local address
From: http://en.wikipedia.org/wiki/Unique_local_address
In the Internet Protocol Version 6 (IPv6), the address block FE80::/10 = 1111:1110:1000 has been reserved for link-local unicast addressing
Generation of Link-Local Address in Windows
From:https://technet.microsoft.com/en-us/magazine/2007.08.cableguy.aspx
IPv6 Autoconfiguration Behavior for Windows Vista Computers running Windows Vista® or Windows Server® 2008 by default generate random interface IDs for non-temporary autoconfigured IPv6 addresses, including public and link-local addresses, rather than EUI-64-based interface IDs. A public IPv6 address is a global address that is registered in DNS and is typically used by server applications for incoming connections, such as a Web server.
Generation from MAC address EUI-48
From: http://packetlife.net/blog/2008/aug/4/eui-64-ipv6/
48 bits + 16 as follows Organizationally Unique Identifier (OUI) and FFFE and the NIC specific part.
Unique Local Address (ULA)
From: http://en.wikipedia.org/wiki/Unique_local_address
In October 2005, RFC 4193 was published, reserving the address block fc00::/7 for use in private IPv6 networks and defining the associated term unique local addresses. DEPRECIATED: fec0::/10 for site-local addresses
Solicited Node Multicast Group and Neighborhood Discovery
Network Discovery - Multicast - DAD (Duplicate Address Detection)
From: https://www.youtube.com/watch?v=O1JMdjnn0ao
Arc form IPV4 becomes Neighborhood Discovery in IPV6 Computer and devices are found through Neighborhood Solicitation (NS - 135) and Neighborhood Advertizement ( NA - 136) Network connections automatically join the Solicited Node Multicast Group based on last 24 bits xx:xxxx FF02::1:FFxx:xxxx = FF02:0000:0000:0000:0000:0001:FFxx:xxxx Network connections automatically join the Global Solicited Node Multicast Group FF02::1 = FF02:0000:0000:0000:0000:0000:0000:0001 FE80:: Link Local 2xxx:: Global Unicast 3xxx:: Global Unicast FFxx:: Multicast
IPv6 Tools Private ipv6 Address Range
Private ipv6 address range
From: https://www.sixxs.net/tools/grh/ula/
IPv6 ULA (Unique Local Address) RFC4193 registration This page allows you to generate and then 'register' your IPv6 ULA (Unique Local Address) RFC4193 prefix. Note that this does not concern ULA-Central, though this system could easily handle that too. When you have registered your ULA prefix here, it allows others to check up if they accidentally generated the same prefix, before using it. This should absolutely minimize the number of collisions for ULA space. We hope that everybody using ULA prefixes register their prefixes here, to avoid these collisions.
https://www.ultratools.com/ipv6Tools
The UltraTools IPv6 provide calculators,IP address converters and real-time lookups to assist you with your day-to-day system administration tasks.
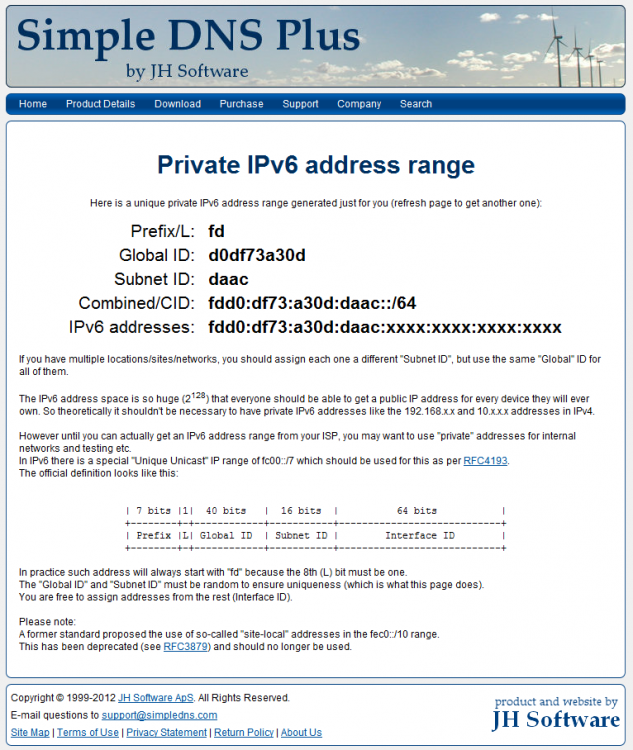
http://www.simpledns.com/private-ipv6.aspx
Here is a unique private IPv6 address range generated just for you (refresh page to get another one): In IPv6 there is a special "Unique Unicast" IP range of fc00::/7 which should be used for this as per RFC4193. The official definition looks like this: | 7 bits |1| 40 bits | 16 bits | 64 bits | +--------+-+------------+-----------+----------------------------+ | Prefix |L| Global ID | Subnet ID | Interface ID | +--------+-+------------+-----------+----------------------------+ In practice such address will always start with "fd" because the 8th (L) bit must be one.